To help protect platforms and data, and enable developers to build more trusted applications, Intel® Security Essentials offers a framework of hardware-based security capabilities across Intel® processor lines. Intel Security Essentials core capabilities seed solutions leveraging hardware-rooted security in a consistent way in a variety of security usage models. The lower cost and consistent implementation continues to encourage the rapidly growing adoption of hardware-rooted security in devices, networks, and cloud platforms.
Figure 1. Security at the core.
Today, implementing hardware-based security is a widely recognized best practice compared to software-only based approaches. However, the complexities of enabling systems with discrete hardware security components from multiple vendors creates design, deployment, and operational barriers that can hinder adoption. With multiple discrete hardware security components, each with different and disconnected root-of-trust capabilities, it may not be possible to fully integrate the components’ security capabilities into a cohesive security architecture. The result is often a fragmented solution with significant barriers for upgrades, post-deployment.
The industry is moving to a software-defined model where applications and workloads span devices and servers running at the edge (Internet of Things and fog) to data center platforms running in the cloud. So, the need for consistent and reliable security implementations is greater than ever.
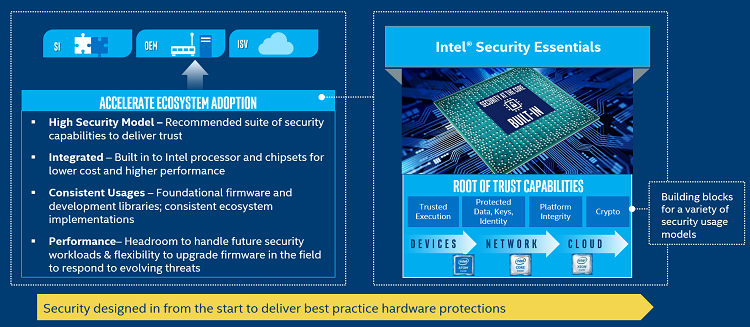

Figure 2. Intel® Security Essentials.
After implementing a multi-year roadmap, Intel has converged our key root of trust security capabilities across all our processors and chip sets. Intel’s existing processor security technologies can be enabled to deliver these baseline protections. These building blocks form a recommend suite of baseline hardware protections that should be used by the ecosystem to deliver a variety of security usage models. This common set of capabilities include:
- Crypto: Hardware-assisted crypto acceleration and secure key generation
- Protected Data, Keys, and Identity: Encryption and storage for sensitive data, keys, or credentials, at rest and in transport
- Platform Integrity: Protected and verified boot process with hardware attestation of the platform
- Trusted Execution: Isolated enclaves that protect shared secrets, code, or sensitive data in the application runtime
Intel embarked on this effort to accelerate the adoption of best practice hardware protections and to drive consistent security models that speed development. Intel is committed to delivering a write once run anywhere model for security. Intel seeks to equip developers with the same four capabilities on the processor, regardless of whether the goal is to secure a cloud platform or an Internet of Things (IoT) device.
With zero incremental cost beyond the system-on-a-chip (SoC) from Intel itself, Intel Security Essentials gives the ecosystem a more cost-effective and performant option. These designed-in capabilities also deliver the flexibility to upgrade firmware and repurpose devices to face future threats, or to address new security use cases.
Intel is uniquely positioned to influence and promote a consistent hardware security model across a broad ecosystem. Intel Security Essentials is based on a consistent architecture, with integrated firmware, development libraries, and validation on wide variety of operating systems. Intel’s general-purpose systems-on-a-chip (SoCs) with integrated security offer a new way forward to implement hardware-based security.
Intel will continue to innovate new technologies to implement the foundational capabilities of Intel Security Essentials. Stay tuned throughout 2018, as Intel business units bring out references to Intel Security Essentials in their platform security architectures and portfolios.
Explore Intel Security Essentials technologies and use cases, visit the Intel® hardware-enabled security page
Related Content
Intel® Secure Device Onboard (Intel® SDO) Scales Devices to IoT Platforms: Intel and Arm* are collaborating on a shared vision to connect any device to any cloud.
Intel and Arm Share IoT Vision to Securely Connect ‘Any Device to Any Cloud’: As we enter this accelerated growth phase for IoT, we will continue to collaborate with technology vendors to provide customers more protections that they need.
About the Author
 Lorie Wigle is vice president of Intel Architecture, Graphics and Software, and general manager of Platform Security Product Management. Follow @LWigle on Twitter* and keep up with her team’s developments at @IntelSecurity.
Lorie Wigle is vice president of Intel Architecture, Graphics and Software, and general manager of Platform Security Product Management. Follow @LWigle on Twitter* and keep up with her team’s developments at @IntelSecurity.